Mastering VAPT Frameworks: Unleashing the Guardians of Cybersecurity
By Prempal Singh
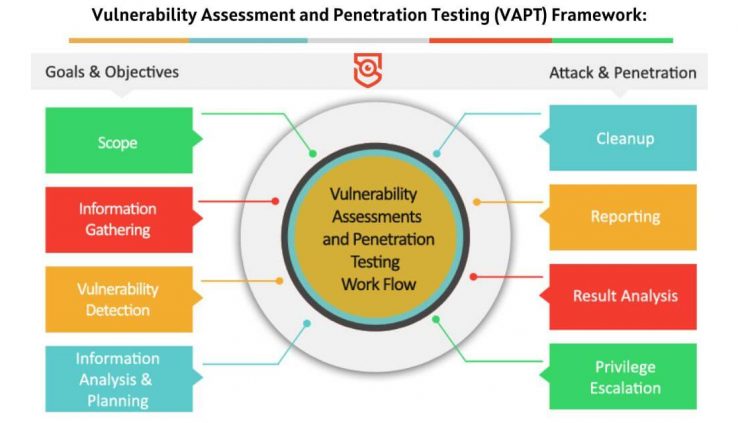
Introduction In today’s interconnected world, cybersecurity is of paramount importance. Organizations, regardless of their size or industry, must proactively identify and mitigate vulnerabilities to protect their systems, data, and reputation. Vulnerability Assessment and Penetration Testing (VAPT) frameworks provide a systematic and comprehensive approach to evaluate the security posture of an organization’s digital assets. In this […]