Useful sites and services in the TOR network
By Prempal Singh
In simple words, TOR is a network where the user completely retains his anonymity on the Internet. It does not really matter what he will do – to visit sites, keep his own blog, send messages.
Anonymity of traffic is possible due to the use of a server network distributed throughout the world with redirection to dozens (and in some cases hundreds) of nodes. Anyone who downloads the TOR browser and installs it on a computer can use the capabilities of such a network .
Why can TOR technology be useful?
There are several reasons why anonymity may be necessary:
- access to sites,
- blocked by regional providers;
- unwillingness to disclose information about the computer and its location;
- Hiding personal data and securing information on your PC.
The basic principles of the network TOR
To understand what TOR is, you need to understand how the system works. It consists of several main nodes:
- Input or watchdog – with the help of this node is the direct entrance to the network. As a rule, input nodes are stable and high-speed servers.
- Intermediate – designed to transfer information from the input node to the output, making it almost impossible to track all movements of information. The number of intermediate nodes is constantly changing and in some situations can go up to several hundred.
- The output is the point used to send traffic to the user.
Useful sites and services in the TOR network
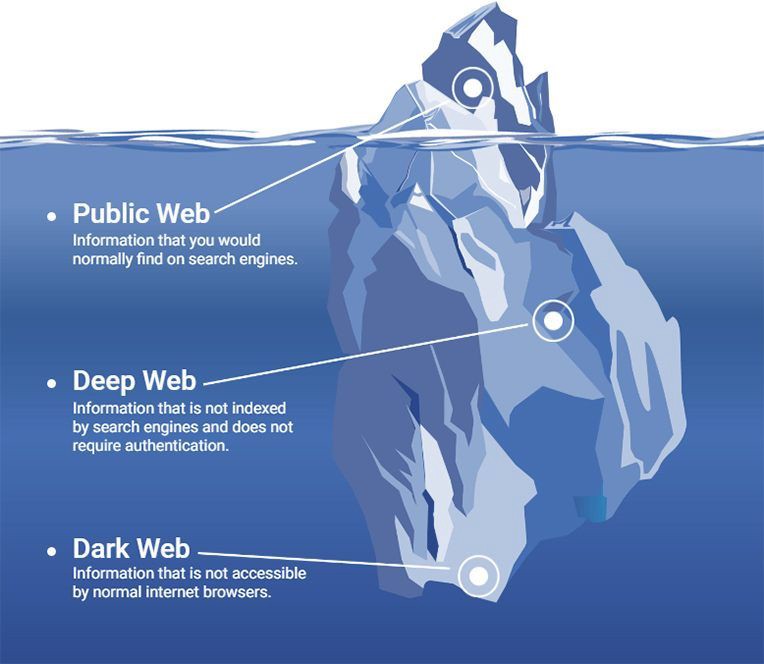
The daily audience of TOR exceeds 2 million users, and in the .onion domain there are about 100,000 addresses used by various services. In this article I will show only a small part of the sites that may be useful to you if you use TOR.
It is quite difficult to imagine an array of 100 thousand websites. Those who use TOR every day may think that this number is not exact or exaggerated. On the other hand, it is important to understand that the TOR network does not consist solely of sites that use the HTTP protocol.
There are tens of thousands of SSH, FTP, SMTP, Bitcoin, XMPP, Ricochet, and IRC servers using .onion addresses for anonymity or convenience. Most of these servers are password protectedor not accessible to a wide audience.
In addition, it should be borne in mind that about 2 million people use TOR daily, and if at least 5 percent during a day want to register a name in the .onion domain, then we will already get 100 thousand unique addresses. In short, a list of 100 thousand in size no longer seems so unrealistic.
Who uses TOR?
Many reputable organizations and publications, such as EFF, The Guardian, Forbesand Gizmodo promote TOR to the masses. The main misconception is that this network is used exclusively by attackers of various stripes. Let’s try to figure out who those 2 million people use TOR every day. According to the official website, TOR uses:
Ordinary people. The two most common reasons why TOR is popular are bypassing censorship and protecting against mass surveillance. World news, articles about culture, health issues, religion, and other information sources may not be available due to the state firewall, which can be bypassed using TOR. In addition, Internet providers often sell information on the history of visiting sites to marketers, and here TOR also comes to our aid.
Journalists and their audience. TOR is part of the SecureDrop open source awareness system that information agencies can use to securely transfer documents and interact with anonymous sources. Many respected news agencies use SecureDrop.
Employees of power structures. TOR allows security forces to be closer to intruders, which helps to trap drug dealers, hackers and other criminal elements.
Activists and informers. Human rights activists use the TOR to anonymously send information about various kinds of violations that take place in various territories, including those that are traditionally considered dangerous to visit. At the international level, labor rights activists use TOR and other means for online and offline anonymity to unite people in accordance with the World Declaration of Human Rights. As you understand, being within the law does not always guarantee security, and TOR allows people to express their opinions and at the same time remain anonymous.
I will talk about dozens of useful websites with .onion addresses that are publicly available. Some of these sites are also available without using TOR. In compiling this list, I did not aim to collect all the darknet’s cream, but I wanted to find the most useful resources that everyone in the era of mass surveillance can use on a daily basis to improve their security and anonymity.
Warning: None of the sites on my list was checked for legitimacy. You need to be overly attentive when browsing the sites listed below, and especially downloading content from these resources. Moreover, I personally do not give preference and do not try to advertise any of the above services. All sites were taken from public sources and specialized public directories.
1. Search Systems for TOR Network Resources
There are many search engines that allow you to find the desired content on the TOR network. As in the case of Google, these search engines index the .onion addresses and, thus, replenish their databases.
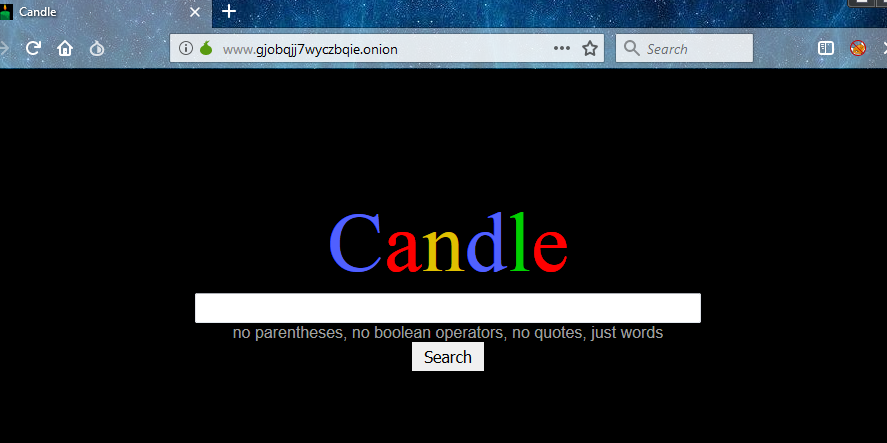
- Candle: A minimalist search engine for .onion addresses without the support of round brackets, boolean operators and quotes. You can only enter words.
- Grams: Search among job offers, as well as digital and physical goods that you can buy using bitcoins and other currencies.
- Haystack: It is claimed that the database of this search engine contains more than 1.5 billion pages with 260 thousand sites that have addresses in the .onion domain (this also includes non-existent sites).
- Not Evil: A search engine with an index that contains more than 32 million links to .onion addresses.
- Torch: A search engine with 450 thousand links.
- Tor Onionland: A search engine based on about 5 million pages with 57 thousand sites.
-
- Confidant: An alternative to standard open source email with an anti-spam feature. All messages are encrypted and Confidant administrators will not be able to access the content.
- Daniel Email: Free and anonymous email. The total amount of storage for each account does not exceed 25 MB.
- Elude: Supports encryption of emails. Access to mail is carried out exclusively through the web client and the TOR network.
- GuerrillaMail: Free one-time email with built-in antispam.
- Mailpile: A modern web client with integrated PGP encryption that simplifies secure communications.
- ProtonMail: The easiest-to-use open source client with a modern web interface. All emails between ProtonMail users are automatically encrypted.
-
Riseup: The Riseup development team is in Seattle, who stand up for freedom of expression and are fighting any kind of harassment. The service is available through the TOR network.
2. Search engines on regular sites
Google collects and accumulates data using various tools (Google Analytics, Google Fonts) and tracks user activity on the Internet through IP addresses and cookies (cross-domain tracking). However, there are search engines that allow you to search the Internet anonymously and without linking search queries to Google’s account or other personal data.

Below is a list of some search engines that allow anonymously find resources on the Internet.
- DuckDuckGo: Internet search engine similar to Google, allowing you to keep your privacy while searching.
- SearX: a feature-rich meta-search engine that accumulates search results from multiple search engines, allowing you to get the most accurate results. Searx supports more than a hundred search engines, including DuckDuckGo, Bing and StartPage. Moreover, Searx allows you to create advanced search queries using various operators.
- TPB: allows you to search and download software and media files for free.
3. Security and privacy
The following resources contain helpful guides to protect against online surveillance. Many sites will be useful to people who are not very savvy from a technical point of view. Other resources are intended for a more advanced audience. At some addresses you can find useful information to bypass surveillance and increase stealth actions ( OPSEC).

OpenPGPKeysever: A repository for PGP keys that allows you to anonymously retrieve keys for secure communications and authenticate.
- Privacy International: A London-based charity that acts in opposition to government authorities, advocates for comprehensive digital protection and fights human rights.
- Security in a Box: Contains many instructions for installing and using software and services for digital protection.
- SKS OpenPGP: Another tool that allows you to anonymously download keys for secure communications and authenticate.
- TorProject: A network of servers supported by volunteers that helps organizations and people share information anonymously.
- Whonix: A platform where userscan chat with developers and other members of the public about security issues through a forum. In addition, there are also many OPSEC manuals.
4. Analogs of Pasterbin
Services like Pasterbin allow you to publicly (or privately) share your code and other information with friends and colleagues. Unlike pastebin.com,most of the similar services on the TOR network automatically delete what you posted in a few weeks.
-
-
-
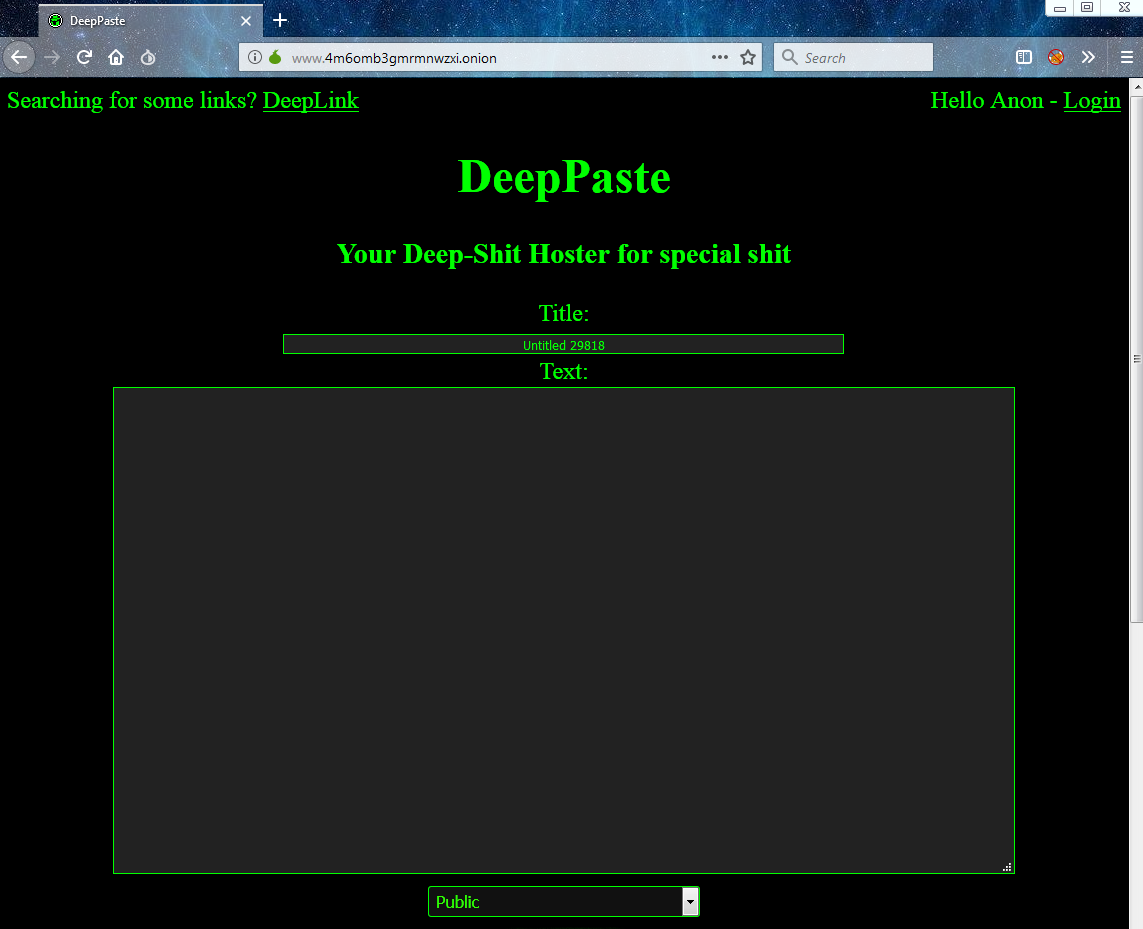
- DeepPaste: The simplest pastebin, which provides for the self-destruct function of what you have shared. The creators claim that they never delete or censor the laid out information.
- Felixxx: A little known service equivalent.
- Riseup Paste: Laid out automatically deleted during the week and can not exceed 50 MB.
- Pasta: An open source Pasterbin with a download limit of 10 MB. Features self-destruct.
- Stronghold Paste: Service created by Sayak Banerjee. An open source web application that is one of the long-livers among such services.
- ZeroBin: Open source minimalistic pastebin. Layout is not available to service administrators, because the information is encrypted.
5. News sites
In some countries, Internet access is severely curtailed, which seriously complicates access to some news sites.
-

-
-
-
- The New York Times: In October 2017, an announcement appeared announcing that nytimes.comwould be available through the TOR network.
- Propublica: A non-profit and independent association of journalists broadcasting on technology, government, business, criminal justice, the environment and immigration.
6. Email
There are several reasons why you might want to use e-mail through TOR. First, it is much more difficult to track traffic on a TOR network. Secondly, TOR allows you to hide the real IP address and location from the email provider.
Confidant: An alternative to standard open source email with an anti-spam feature. All messages are encrypted and Confidant administrators will not be able to access the content.
- Daniel Email: Free and anonymous email. The total amount of storage for each account does not exceed 25 MB.
- Elude: Supports encryption of emails. Access to mail is carried out exclusively through the web client and the TOR network.
- GuerrillaMail: Free one-time email with built-in antispam.
- Mailpile: A modern web client with integrated PGP encryption that simplifies secure communications.
- ProtonMail: The easiest-to-use open source client with a modern web interface. All emails between ProtonMail users are automatically encrypted.
- Riseup: The Riseup development team is in Seattle, who stand up for freedom of expression and are fighting any kind of harassment. The service is available through the TOR network.
- drksh: Hackers personal blog and Git repository.
- Jamie Scaife: Notes are published regarding the secure use of public Wi-Fi, site encryption, .onion services, operating systems, and Linux installations.
- Sarah Jamie Lewis: Sarah is involved in several projects:OnionShare (mentioned above in the section “Security and Privacy”), Ricochet, and other research that helps developers better understand how TOR and onion services work.
- Comic Books: A huge list of comics that are not protected by copyright. However, there may also be illegal material. Be careful.
- Imperial: An open source repository where e-books are storedwithout DRM protection. It is possible to upload your own books to supplement the collection. There may be copyrighted material in the repository. Be careful.
- Z-Library: The creators claim that Z-Lib is the largest library in the world, containing more than 3.4 million books available for download. There may also be copyrighted material.Traudt: A research project of naval personnel that covers topics related to TOR development and issues related to the Internet as a whole.
7. Blogs and personal sites
There are many developers and enthusiasts who regularly share their discoveries and findings in personal blogs.
- drksh: Hackers personal blog and Git repository.
- Jamie Scaife: Notes are published regarding the secure use of public Wi-Fi, site encryption, .onion services, operating systems, and Linux installations.
- Sarah Jamie Lewis: Sarah is involved in several projects:OnionShare(mentioned above in the section “Security and Privacy”),Ricochet,and other research that helps developers better understand how TOR and onion services work.
- Traudt: A research project of naval personnel that covers topics related to TOR development and issues related to the Internet as a whole.
-
8. Libraries
Most of the libraries that are in the TOR network allow you to download materials without any restrictions, which, on the one hand, can be useful to people living in many countries, and on the other, contradict legislation. The sites listed below store copyrighted content, unlicensed content, as well as content licensed under Creative Commons and other freely available media files. Remember that some materials may be illegal, and do not forget to pay the authors and companies who own the copyright. We are against piracy.
- Comic Books: A huge list of comics that are not protected by copyright. However, there may also be illegal material. Be careful.
- Imperial: An open source repository where e-books are stored without DRM protection. It is possible to upload your own books to supplement the collection. There may be copyrighted material in the repository. Be careful.
- Z-Library: The creators claim that Z-Lib is the largest library in the world, containing more than 3.4 million books available for download. There may also be copyrighted material.
9. Social networks
Anonymous registration on social networks like Facebook can be extremely difficult. It is for this reason that many alternative social networks have been created in the TOR network, where everyone can register anonymously and freely express their point of view.
- Cyph Messenger: Video chat with open source. Also available is a file transfer function like in applications like Skype.
- DNM Avengers: A forum where questions are discussed and reviews related to pharmaceuticals are published.
- Dread: Analog Reddit. In addition to discussing general issues on Internet-related topics, discussions are held and reviews regarding pharmaceuticals are published.
- Facebook: Access Facebook through the TOR network.
- Hidden Answers: One of the analogues of the Stack Overflow site, where users can anonymously ask questions about hacking, security and privacy, cryptography, commerce, government, etc. This site appeared in mid-2015, is one of the veterans among similar onion services and is still available.
- Smuxi: Free and convenient IRC client.
- Suprbay: The official forum of the tracker The Pirate Bay.
- TheHub: A forum where news, issues related to pharmaceuticals and safety are discussed. Created by anonymous users.
10. Hosting
There are many hosting providers in the TOR network. There are hundreds of sites for storing pictures, notes, files, pastebin’ov and entire .onion sites.
- Black Cloud: Service for downloading files. The creators claim that all files are encrypted.
- Daniel Uploads: Another service for uploading files (maximum size 10 GB). Uploaded content is available to all.
- dhosting: Free and anonymous hosting. There is support for PHP, MySQL, FTP and your own .onion addresses.
- I mage Hosting: Free hosting for pictures with support for PHP, MySQL, PHPMyAdmin, encrypted storage, own .onion addresses. Available free space – up to 2 GB.
- OnionContainers: Secure hosting with support for Nginx,PostgreSQL and WordPress based blogs.
- 0ut3r Space: Downloaded files are automatically deleted after 14 days. File size should not exceed 200 MB.
- PopFiles: The simplest hosting for files with the ability to create your own URLs. Downloadable file should not exceed 500 Kb.
- Riseup Etherpad: An open source editor with many options. Designed for teamwork in real time.
11. Operating systems
There are several operating systems sharpened for security and privacy that can be downloaded anonymously.
- Debian: A free and easy-to-use operating system that is supported by collective enthusiasts.
- Qubes: A free, open source operating system where the focus is on security. Qubes implements the ideology of “security through separation”, where users can create several isolated environments for different needs.
- Whonix: An operating system for those who especially care about their privacy and security. This OS is built into the default use of TOR and isolation of streams to protect against mass surveillance and the collection of user data (see also Security and Privacy).
12. SecureDrop
SecureDropis an open source system that allows you to anonymously and securely accept documents from various sources. Mainly used by news agencies, including The New York Times, The Washington Post, ProPublica, The New Yorker and The Intercept.
- The Guardian: A British daily newspaper that was awarded the Newspaper of the Year award four times at the annual British Press Awards event. The last time the prize was awarded was in 2014, because the newspaper was one of the first to report on state surveillance.
- The Intercept: This news agency appeared in 2014 and was originally conceived as a platform for publications based on documents laid out by Edward Snowden. Since then, the publication adheres to the direction of “antagonistic journalism.”
- NPR: American non-profit news agency supporting more than 1,000 public radio stations.
- VICE: Digital media content company. It covers topics related to politics, entertainment, pharmaceuticals and technology.
13. Bitcoin mixers
Bitcoin transfers are not 100% anonymous. Mixers are used to mix your biotcoins with other people’s Bitcoins in order to hide the source of the translation. When “mixing” the currency, your money is sent to an anonymous service, and in return money of the same volume from another person is sent. In short, the purpose of a mixer is to make it difficult for companies and government agencies to track transactions.
Warning: I would like to remind once again that none of the links cited has been verified for legitimacy. Act with extreme caution when hiding transfers in Bitcoins using mixers.
- Bitblender: It is claimed that this service takes small and random commissions, has a bonus and referral program, two-factor authentication via PGP, up to five joint deposit addresses, fast processing, no logs and automatic withdrawals.
- BitCloak: This service has a free API. There are also random commissions in the region of 2% and a commission of 0.0004 Bitcoin for each address for transferring funds.
- Blockchain: Little is yet known about this service.
- CryptoMixer: Instant mixing, no logs, the minimum transaction size is .001 BTC, referral program andflexible feesdepending on the size of the transaction.
- Elude: The service takes random commissions in the range of 1-3% of the transaction size.
- PrivCoin: The service supports multiple cryptocurrencies.
14. Miscellaneous
TorMetrics is one of many useful sites based on TheTorProject, Debianand Riseup. Below are sites that do not fall into any of the above categories, but which may be useful to readers.
- CloudFlare: Private DNS client (resolver). The creators say they never sold or abused user data.
- ExpressVPN: VPN service.
- ExoneraTor: A database containing IP addresses that are connected (or were connected) to the TOR network.
- Fingerprint Central: A service that collects browser data that helps developers protect themselves from browser-related deanonymization techniques.
- jRAT: Cross-platform malware (currently not working).
- Keybase: A public key database (GPG), a secure messaging application, and a code reloading platform (Git).
- · Njalla: Private domain registrar, allowing anonymous registration and purchase for cryptocurrency.
- SMSPrivacy: An anonymous SMS-service that allows registration and purchase of subscriptions for cryptocurrency.
- TorMetrics: Analytical utility designed to collect and visualize statistics on the TOR network. Helps developers better understand how TOR works, and find possible similar traffic patterns arising in the network.
- Tor Nyx: A set of command-line utilities that help users get information and configure instances of TOR applications running on computers and servers.
- 0day: Database exploits. There are exploits for sale that can be bought for bitcoins.
15. Catalogs of onion sites
The relevance of the list of onion-sites is monitored by special spider programs that periodically check their database for non-working addresses. Sites that are offline for a long time are deleted from the database and directories.
Below is a list of several directories that will help you maintain current lists of onion addresses.
- Daniel’s onions: A database of 7,000 addresses.
- Fresh Onions: An open source directory with over 5,000 unique addresses.
- onionsoup: Verified list of dozens of onion services.
- UnderDir: A database of 25,000 onion services, most of which are not available.
- VisiTOR: A database of 5,000 addresses.
CB3ROB: A database containing about 4,000 working onion sites (currently not working).
-
Conclusion
Most onion services disappear a few hours after they appear, as these services appear for testing and experiments with TOR. This fact provides a unique opportunity for those who want to quickly and anonymously share information online. On the other hand, those who seek legitimate content may experience difficulties during the search. Anyone using an inexpensive system based on Android or Raspberry Pican anonymously create their own personal corner on the Internet. Without the need to provide personal data, registration, monthly subscriptions and payment to third-party providers.
-
-
