Media File Jacking
By Prempal Singh
According to new research by Symantec have shared a detailed report regarding a media file jacking flaw threatening Android apps. According to their research hackers can simply manipulate media files transferred over WhatsApp, Telegram, and Android applications. Neither the sender nor the receiving user would ever notice this manipulation. The attack does however only work under certain conditions.
As we know that some android apps store media files in storage(internal & external) by default, like WhatsApp for Android by default automatically stores media files in external storage, while Telegram for android uses internal storage.
Hackers can manipulate incoming files on an infected device even before the recipient user actually sees them. This is possible because of a certain time-lapse during the writing of media files on the disk and the following UI prompt.
Media file jacking attack (working)
Just like man-in-the-disk attacks, from the recipient, a malicious app installed on a device can intercept and manipulate media files, such as private photos, documents, or videos, sent between users through the device’s external storage all without the recipient’s knowledge and in real-time.
The flaw is originated from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface for users to consume.
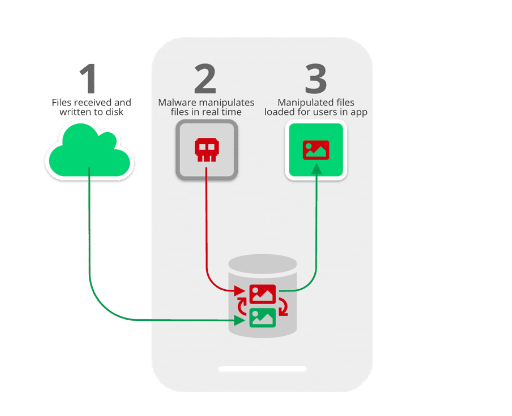
As seen in the image above, in the time between when files are first received on a device and written to the disk (STEP 1), and when they are loaded for users to consume via the apps (STEP 3), malware can instantaneously analyse and manipulate the files (or just replace them with the attacker’s chosen files) for malicious gain (STEP 2).
The thumbnail that occurs in the notification that users see will also show the manipulated image or file, so recipients will have no sign that files were changed. What’s terror-stricken is that the data can be manipulated on WhatsApp both when sending files (which means the attack is launched on the sender’s device) and when receiving files (that is, the attack is happening on the receiving device).
How to be safe from this security flaw?
WhatsApp and Telegram users can mitigate the risk by disabling the feature that saves media files to external storage.
In WhatsApp, saving media files to external storage can be disabled by navigating to
Settings -> Chat -> Media Visibility
Telegram, it can be disabled by turning off ‘Save to Gallery’ through Settings -> Chat Settings -> Save to Gallery.
