What is PCI DSS Compliance?
The PCI Digital Security Standard (PCI DSS) is a collection of security guidelines that have achieved international recognition for safeguarding the confidentiality of sensitive information associated with payment accounts. These guidelines apply to any company or other institution that handles cardholder information. By being PCI compliant, you can defend your company from losing clients, damage to your reputation, lawsuits, and significant financial damages.
What is the most current version of PCI DSS Standards?
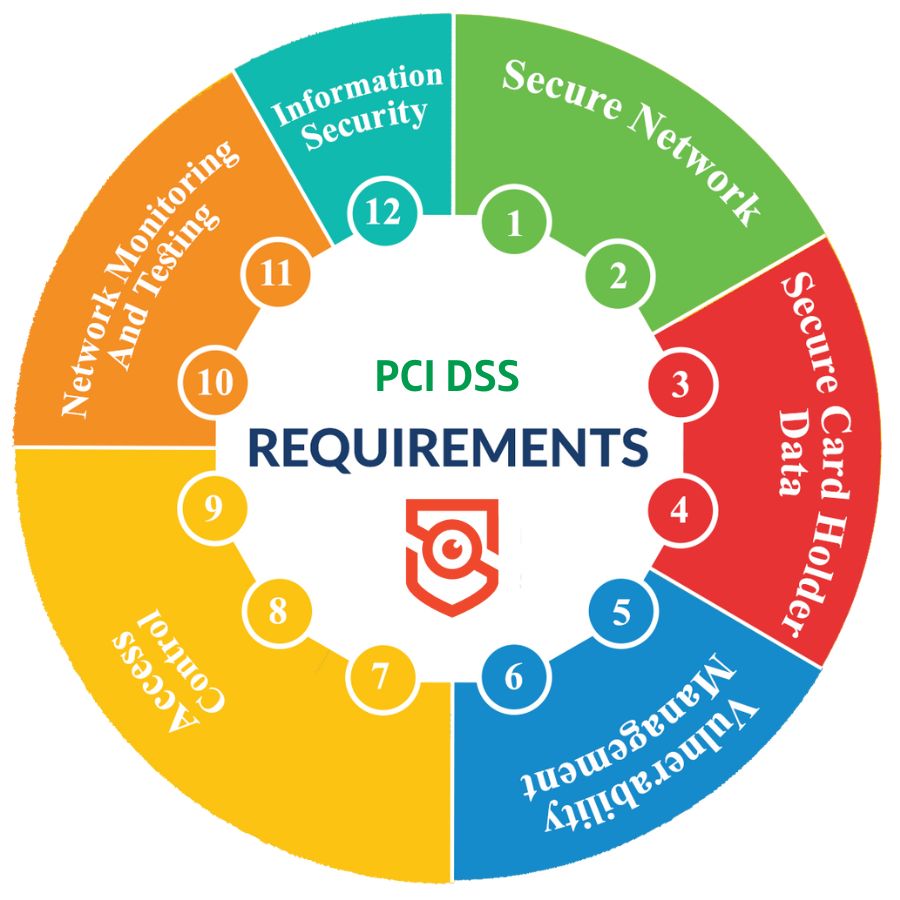
PCI DSS v4.0 is the most recent version of these standards as of March 2022. However, v3.2.1 will be valid until the end of March 2024. The PCI DSS outlines 12 standards, testing protocols for all PCI DSS Requirements, and implementation best practices.
How Can I Become PCI Compliant?
To be PCI compliant, a company must set up and uphold security practices that meet or exceed certain standards. The PCI compliance services provided by Cyberops will help your business through this procedure and keep it compliant all year long. We will help you in completing the compliance process quickly and completely, giving you the assurance that your data is secure and, more importantly, that the data of your customers is protected.
Why is PCI DSS Compliance Important?
If you are a merchant who takes credit card payments or a merchant service provider, your business is responsible for protecting cardholder data through PCI safety requirements and PCI solutions. With security breaches and cybercrime on the rise, complying with PCI DSS Requirements is essential to keeping your customer's payment card information safe and secure.
Which card must details be protected after being stored?
Merchants and service providers can store cardholder information in line with PCI DSS standards. These include- Cardholder information (main Account Number, Cardholder Name, expiration date, and service code) and sensitive authentication data (whole track data, magnetic stripe data or its chip counterpart, CAV, CVC, CVV, and CID numbers, as well as PINS and PIN blocks).
What falls under a PCI DSS assessment's scope?
Any systems included in or connected to an organization's cardholder data environment (CDE) must comply with the PCI DSS Requirements. The CDE includes all individuals, parties, and systems that handle, process, or communicate sensitive authentication information and cardholder data. Depending on how well the CDE has been compartmentalized, PCI DSS is applicable to all areas of a company or only a portion of it. Networking hardware, servers, computational hardware, and software are all included as system components.
What Happens if a Company Is Not PCI Compliant?
When PCI security rules are not followed, weak security measures can expose sensitive cardholder data to attack. Moreover, non-compliant organizations could be liable for extra penalties, audit and investigation fees, and card replacement charges in the event of a security breach or attack. A company's reputation can suffer if PCI DSS compliance is not enforced, particularly if a data breach does take place.
What is an SAQ for PCI DSS Compliance?
Based on an organization's card transaction volume and transaction categories, it can use an SAQ (self-assessment questionnaire) to self-assess its PCI Data Security Standard compliance. SAQs include questions about card data security. You may have to set up a number of the PCI data security standard's requirements and controls depending on your SAQ. Cyberops helps small and big enterprises identify and implement PCI compliance requirements.



 1
Encryption Key Management Policy
1
Encryption Key Management Policy
 2
Firewall/router configuration
2
Firewall/router configuration
 3
Internal Security Testing Procedures
3
Internal Security Testing Procedures