Microsoft Office documents are used by hackers for targeted phishing and intellience
By Prempal Singh
The specialists of “Kaspersky Lab” was told that in the course of the study target Freakyshelly attack, they managed to find the target sending letters with interesting embedded documents. These were the files in OLE2 format which did not contain macros, exploits, or any other active content. A closer look revealed that inside there are several references to the PHP-script, located on the third-party resources. When you try to open these files in Microsoft Word turned out that the application connects to one of these links. As a result of treatment attackers received information about the software installed on your computer.
Researchers are interested in what is happening, because it was not clear why such a thing could be necessary attackers. But for successful targeted attack, you must first conduct a reconnaissance – to find a way to the alleged victims and to collect detailed information about them. For example, find out which version of the operating system and some applications on the victim’s computer to then send the appropriate exploit targets.

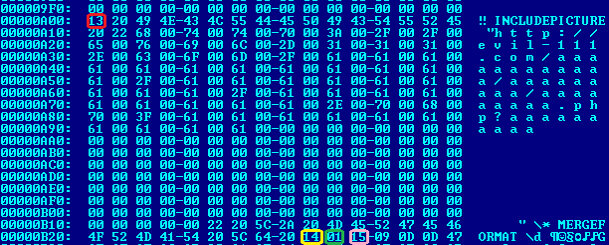
Experts “Laboratory” decided to find out why the Office goes on the link and how can I find such references in documents. So, in the files, it was found INCLUDEPICTURE field with one of the suspicious links. However, Word does not address her.
Analysts write that the data block in the picture above – the first and only piece of text in the document. Text in Word document format is in Word Document flow in the “raw”, without any formatting, except for the so-called fields. Field say Word, that a certain part of the text should be displayed when you open the document in a special way, for example, thanks to the visible clickable links to other pages of the document, URL, and so on. INCLUDEPICTURE field reports that certain characters in the text snap a picture.
The problem was that the INCLUDEPICTURE field description in MS is virtually no documentation, it says only: 0x43 INCLUDEPICTURE Specified in [ECMA-376] part 4, section 2.16.5.33. In fact, in the ECMA-376 standard describes only part of the INCLUDEPICTURE to byte-separator. But it does not say anything that might mean the data after it, and how to interpret them.
By studying exactly how attackers use INCLUDEPICTURE field, experts have found an undocumented feature that is present in the Word for Windows, and also in Microsoft Office for iOS and Android. LibreOffice and OpenOffice do not support it: when you open a document in these office suites, treatment occurs to the link.
As it turned out, the reference unknown attackers hidden in the form of SHAPEFILE. Attackers have used a combination of three flags, according to which should be attached to the form of additional data which represent URL, which is already located on the actual contents of the form. Also, the flag was found which prevents you open a document that content is preserved in the document – do not save.