How to Hack the Website | Types of Hacking and Protection from them
By Prempal Singh
How to hack the site. Types of hacking and protection from them.

Want to learn how to hack the website? Or vice versa, find out how you can protect yourself from hacking? Every day, there is a hacking of sites that are deleted or scammers require a ransom. As they say, the last one laughs the one who does Backup.
Some types of attacks will not give you access to the administrative panel or hosting, but they can significantly harm the site.
Despite the fact that it was much easier to create a site than it was ten years ago, it’s still not every developer knows how to protect his site. There are many ways to hack the site, let’s see what they are, and how to protect the site from hacking.
Methods of hacking the site:
- DDOS
- SQl Injection
- XSS
- CSRF
- BackDoor
- Clickjacking
- MITM
- ZeroDayAtack
- SPAM
- Uploads
This is not all methods of hacking the site, but they are the most common. You should never neglect the protection of your site. It’s especially worth thinking about if you have a major project that will sooner or later be attacked. Read up to the end and find out how to hack the site or protect your project from attacks.
How to hack a website – methods and protection from them!
DDoS Attack
It will not give you access to the management of the site, but there is an opportunity to collapse the site, which can bring a lot of harm. If you have a site with a lot of traffic, then of course you do not want to lose a few days in an empty. And then the position in the search engines.

DDOS is a distributed denial-of-service attack. The network resource fails as a result of a number of requests to it sent from different points. Typically, an attack is organized using botnets.
The length of the site’s failure depends on the duration of the attack and on your preparation for this type of defense. As a rule, hosting provides protection from DDOS, but this does not mean that you can relax. This protection can protect against several thousand requests that are sent to your bot-net site, and if there are more?
The best way to protect is to connect CloudFlair. They provide an opportunity to use the resource for free, speed up the site load, and also cache pages. Everything is done in a couple of minutes and does not require any material investment.
SQL Injection

SQL Injection – this type of attack is already obsolete and it is rarely where you can find it. The bottom line is that a request is sent to the feedback forms, which is not processed in any way and gives out the necessary information. For example, in the comment block write a query drop table users, the user table will be cleared.
Protection against this type of hacking is simple, it is to use prepared requests. They do not change in any way, but only take arguments. PDO can be used in many languages, never use the SET NAMES argument, use the encoding in the DSN string (the first PDO argument). Also it is necessary to limit access of users to a DB. It is also always worth making a backup of the database to avoid getting into an unpleasant situation.
XSS (Cross Site Scripting)
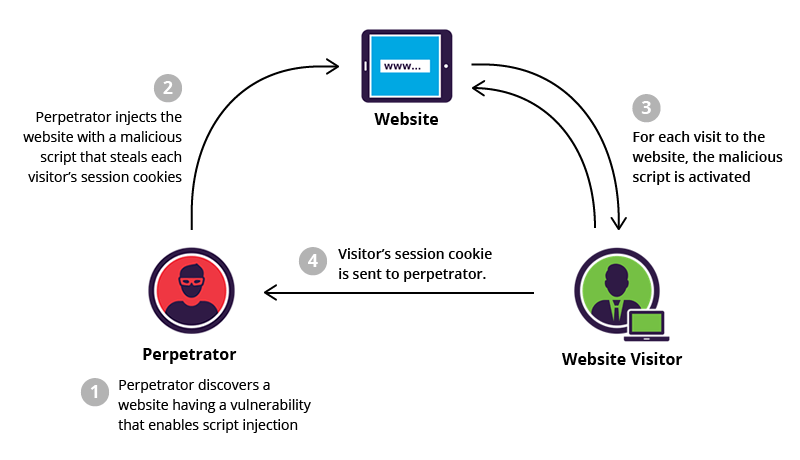
XSS (CSS) – (Cross-Site Scripting) – this kind of attack is all done through the user input. The purpose of this attack is users, not databases. Usually use java script or iFrame. With this type of attack, you can intercept the user’s cookie and log into his account without knowing the password and login. This vulnerability is especially dangerous for commercial sites or Internet attacks. Hacking a site without protection from XSS is very easy, through the same comments.
Protection against XSS attacks can be different, for example, filtering the output from the user input. The easiest way is to put Twig or Blade, protection against this type of attack there is correctly implemented from the “box”.
CSRF (Cross Site Request Forgery)
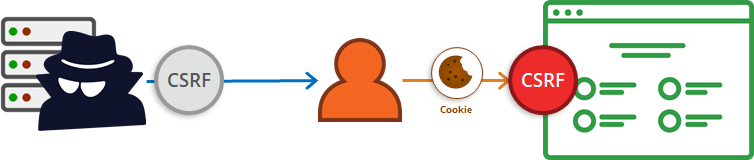
CSRF – (Cross-Site Request Forgery) – enough harmful attack, which can harm people. A frame is created and on the attacked site by clicking in any area an action will occur that can harm users. For example, a message may be sent on your behalf to a friend asking him to send money.
It is very simple to protect against CSRF, just add the CSRF token for the form in the right place. It is saved at the time of the session.
MITM (Man In The Middle Attack)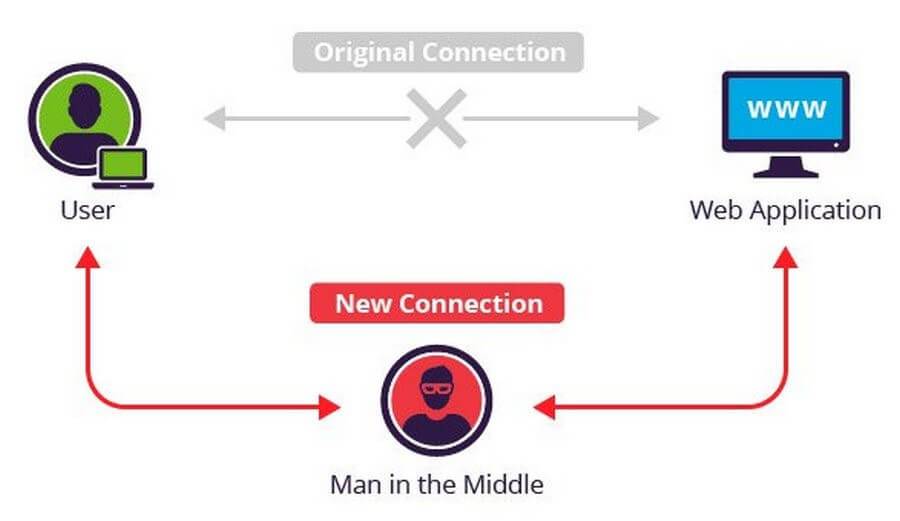
MITM – (Man-In-The-Middle) – a very common type of attack, of which probably everyone has already heard. The essence of the attack is that the person in the middle, he also acts as a hacker, intercepts your packets and replaces them. For example, you send one message to your friend, and it comes another. How to hack a site using MITM? It’s very simple, and it’s very easy to defend yourself! It is enough to add SSL or TLS to your site with a forced download of a site with a secure protocol. If the site can be downloaded with the HTTP protocol, then it means it can be hacked using MITM.
Clickjacking
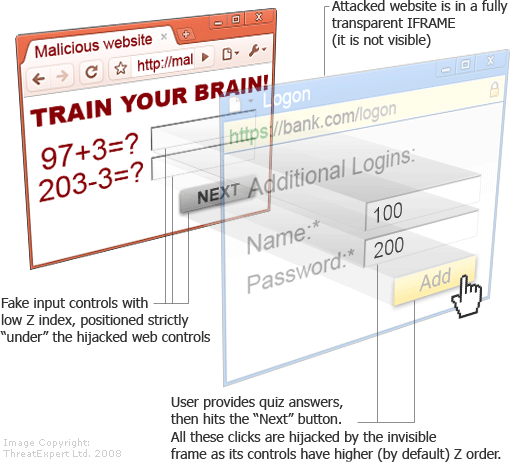
Clickjacking – With a frame that is completely transparent, redirect users to third-party resources. In this way, people do not see it, a button is created that is tied to the cursor and any action on the site will occur when the user clicks on the site. There are a lot of options for protection from this attack, but the most effective way is to use < noscript>.
Brute Force Attack

Brute Force – brute force passwords with a given login or mail. As a rule, the search is not blind, passwords are merged in the database. You can easily defend yourself, put a captcha or limit the number of incorrect login attempts.
Zero Day

ZeroDay – zero day vulnerability. It is that after the release was made a mistake and with the help of it you can hack the site. To ensure that this does not happen to you, always update the technologies used.
Backdoor

Backdoor – encrypted scripts are being introduced into the site, which individually give access to the resource and as a rule they copy themselves to make it more difficult to get rid of them. Check the code for such scripts, do not install third-party plugins that have not been tested and everything will be fine.
Uploads

Uploads – hack a site with the help of downloading files can be, if there is no validation for formats and content. Thus, you can download the script in the avatar and launch it on the site at the link of the avatar. It is required to put a limit on files, as well as change the size of photos, minimally, but this will no longer allow the exchange of intruders encrypted with stenography text.
Subscribe to the site updates, as well as to our Telegram . Also you can support us by simply sharing an article on social networks.
