Dark Web: Everything You Need to Know about the Invisible Web
By Prempal Singh
Dark Web: Everything You Need to Know about the Invisible web
Dark Web – this term refers to a set of websites that are visible in public while having a hidden IP address of the server on which they are located. These sites can be visited by all web users, but it is very difficult to find out who is their author. At the same time, these sites can not be accessed using popular search engines.
Virtually all sites in the so-called Dark Web hide their identity using the Tor encryption tool. Perhaps you know about Tor as a technology that allows users to keep their anonymity on the Internet when visiting sites, blogging, sending messages, etc.
Tor allows you to hide your identity and “replace” your location. In the case where there is a website in the management of the Tor network, the effect is the same as in the situation with the end user. In order to visit the site in the Dark Web, which uses the Tor encryption tool, the web user must also use Tor.
However, not all Dark Web sites use Tor. Some use similar services, such as I2P, but the principle of operation remains the same: the user must use the same encryption tool as the site and, very importantly, know where to find the site to visit it by entering a specific URL. One of the most famous examples of the site of the Dark Web remains Silk Road (“Silk Road”). Silk Road has long been an anonymous trading platform for the purchase and sale of drugs.
At the same time, there are legal cases of using the Dark Web: people living in closed, totalitarian societies can use the Dark Web to communicate with the outside world, excluding surveillance of special services for themselves.
Dark web, Deep web
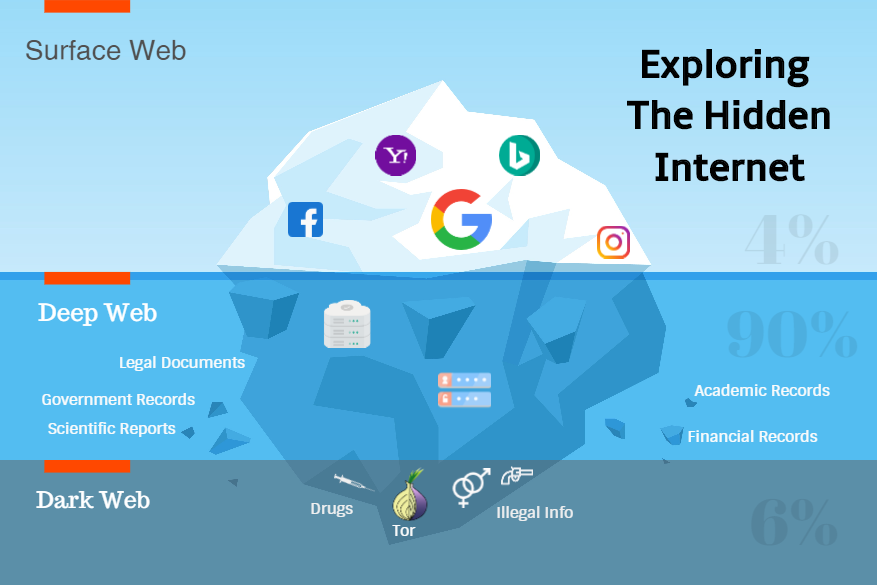
Despite the fact that all these terms are often used interchangeably, they do not mean the same thing. More precisely, Deep Web is a more extensive term that includes the Dark Web, as well as all user databases, web forums that require registration and pages with paid access.
In practice, the concepts of “Dark Web” or “Deep Web” are mainly used to describe a dangerous secret online world. The deep web is a comprehensive term for all web pages that are not indexed for search, the other two terms refer to more specific things.
How to get into the dark web?
Technically, this process is not at all complicated. You just need to install and use Tor. Go to www.torproject.org and download the Tor Browser Bundle, which contains all the necessary tools …
Depending on your use of the Dark Web, some users recommend closing your webcam to guard against prying eyes watching you. After entering the Dark Web, you can be a click away from sites that sell drugs and weapons, and be honest, even the worst things. Do not forget to use the anti-Virus.The dark Internet is the same habitat of the malicious as the visible part of it.
TOP -5 negative moments Tor uses
- You can be watched. The forums are often advised to seal the camera and microphone of the laptop, in order not to become an object of surveillance.
- Using the torus, you can unwittingly become an accomplice in large-scale crimes and hacking activities, as your PC becomes part of the network that is used by other users.
- Tor was developed by the military and special services, which does not exclude its use for their own purposes, despite the promoted brand about 100% safety and anonymity of use.
- It creates inconvenience when using “white” services, for example, by mail. The bottom line is that when you work with Tor, you constantly change the IP address, which leads to the disabling of such services, which perceive this as an attempt of external hacking.
- Google often blocks searches through Tor, because it believes that this is hacking activity. These two services are not created for each other – they are the extremes of the modern cyber world.
About the Author-
Chandan Singh is now working as Sen. cybersecurity analyst at “Cyberops Infosec” in Jaipur, India. Cyberops Infosec is India’s leading cybersecurity company providing VAPT services and ethical hacking training course in Jaipur, India.
