What is Social Engineering? Attacks and Countermeasures
By Prempal Singh

Social engineering – a method of obtaining the necessary access to information, based on the characteristics of human psychology. The main goal of social engineering is to gain access to confidential information, passwords, banking data and other secure systems. Although the term social engineering appeared not so long ago, the very method of obtaining information in this way has been used for quite some time. Employees of the CIA and the KGB who want to get some state secret, politicians and candidates for deputies, and we ourselves, if we want to get something, often without even realizing it, use social engineering methods.
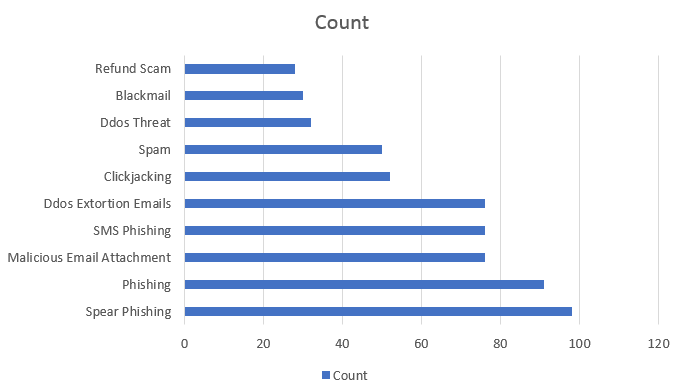
In order to protect yourself from the impact of social engineering, you need to understand how it works. Consider the main types of social engineering and methods of protection against them.
Classification of threats to social engineering (social engineering)
All threats directed at the user through social engineering can be divided into several groups.
- Threats arising from the use of the phone. The phone is the most popular means of communication, therefore it serves as an excellent tool for influencing a person. On the phone it’s easy to impersonate another person, therefore, using actor’s skill, an attacker easily convinces a victim to transfer a certain amount to a bank account or report data. Ways of earning money by sending messages (smashing) and phone calls about winnings in contests, lotteries, requests for money transfer are widespread.
For security, it is advisable to be skeptical of SMS of doubtful character, to ignore the links that come in them. It is necessary to check the identity of the subscriber, use the number identification service.
- Threats emanating from emails (phishing). E-mail can receive letters containing false information from banks and other institutions, forcing to follow the link and enter their personal data. By mail, as well as on the phone, you can receive false requests for help to close people, messages about gifts, winnings and other free bonuses for which you need to transfer money. Secure yourself from intruders by ignoring letters from unknown recipients.
- Threats when using Instant Messaging. Users quickly appreciated the convenience of messaging in real time with the help of Skype, Yahoo !, ICQ, AIM, IRC, etc. Accessibility and speed of this method of communication makes it open for all kinds of attacks. For security, you should ignore messages from unknown users, do not provide them with personal information, do not click on the links.
Subject of impact
Social engineering is not aimed at computer technology, but at its user. All solvent persons, as well as users with valuable information, employees of enterprises and government agencies are of interest.
The method is used to perform financial transactions, hacking, theft of data, for example, client databases, personal data and other unauthorized access to information. Social engineering helps competitors to carry out reconnaissance, identify weaknesses of the organization, attract employees.
Source of threat
Attackers use social engineering to obtain material benefits or to extract data for resale. Social engineering can be used as one of the tools of complex targeted cyber attacks.
The source of the threat can be e-mails, text messages in any messengers, SMS messages and phone calls. Scammers may pretend to be employees of banks and other financial organizations, government employees, law enforcement agencies, Internet service providers, representatives of postal services and large web resources, etc.
Risk analysis
To protect the company from fraud, it is necessary to train the personnel to recognize social engineering and respond to it correctly, to prohibit employees from exchanging passwords or to have one common, to protect client bases and other confidential information, to apply a special confirmation procedure to persons requesting access to any data.
In browsers appeared the option “anti phishing”, warning visitors to the site about the unreliability of this resource. To protect against threats sent in emails, will help spam filters. There is a monitoring service in demand from companies most often attacked by intruders. Reduce the risks of more complex authorization methods.
Countermeasures
The main way to protect against social engineering is training employees. All employees of the company should be warned about the danger of disclosure of personal information and confidential information of the company, as well as ways to prevent data leakage. In addition, every employee of the company, depending on the division and position, should have instructions on how and on what topics it is possible to communicate with the interlocutor, what information can be provided to the technical support service, how and what the employee of the company should inform or other information from another employee.
In addition, we can distinguish the following rules:
-
- User credentials are the property of the company.
All employees on the day of hiring should be explained that those logins and passwords that they were given can not be used for other purposes (on websites, for personal mail, etc.), transferred to third parties or other employees of the company, who do not have the right to do so. For example, very often, on vacation, an employee can transfer his authorization data to his colleague so that he can perform some work or see certain data at the time of his absence.
-
- It is necessary to conduct introductory and regular training of the company’s employees, aimed at increasing knowledge of information security .
Carrying out such briefings will allow the company’s employees to have up-to-date data on existing methods of social engineering, and also not to forget the basic rules for information security.
-
- It is mandatory to have security regulations, as well as instructions that the user must always have access to. The instructions should describe the actions of employees in the occurrence of a particular situation.
For example, in the regulation you can specify what you need to do and where to turn when trying to request confidential information or employee credentials from a third party. Such actions will allow to calculate the attacker and prevent leakage of information.
-
- On the computers of employees there should always be up-to-date anti-virus software.
You also need to install a firewall on your employees’ computers.
-
- In the company’s corporate network, it is necessary to use systems to detect and prevent attacks.
It is also necessary to use systems to prevent the leakage of confidential information. All this will reduce the risk of physic attacks.
-
- All employees should be instructed how to behave with visitors.
Clear rules are needed to establish the identity of the visitor and his escort. Visitors should always be accompanied by someone from the company’s employees. If the employee meets an unknown visitor, he should ask in a correct form, for what purpose the visitor is in this room and where his support is. If necessary, the employee must report unknown visitors to the security service.
-
- It is necessary to limit the user’s rights in the system to the maximum.
For example, you can restrict access to websites and prohibit the use of removable media. After all, if an employee can not access a phishing site or use a flash drive with a “Trojan program” on the computer, he will not be able to lose personal data either.
Proceeding from all listed, it is possible to draw a conclusion: the basic way of protection from social engineering is training of employees. It is necessary to know and remember that ignorance does not absolve from responsibility. Every user of the system should be aware of the danger of disclosing confidential information and know the ways that can help prevent leakage. Forewarned is forearmed!
