What is Cyber Threat and their Types
By Prempal Singh

Cyber threat
It’s illegal entry or the threat of malware intrusion into the virtual space to achieve political, social or other, purposes. Cyber threat can affect the information space of the computer, which contains the information stored materials are physical or virtual appliance. The attack usually affects the storage medium designed specifically for storage, processing and transmission of personal information of the user.
Cyber threats come from hackers, people are able to break into the servers and receive information from them illegally. Hacker is a highly skilled professional who understands the intricacies of computer programs. Historically, that now the word is often used to mean “computer intruder.”
The explosive growth of a wide variety of cyber threats makes today the problem of information security in small and medium-sized businesses more relevant than ever.
It is in this segment of the most acute shortage of qualified of IT-staff, this is where the budget of IT-infrastructure is most often formed as a residual, and finally, it is often simply not available in the Russian SME sector understanding why all this is necessary and how it do.

Agree – is absolutely typical for our country, a picture when all the computers in the company “in charge” a dull student, working at times almost a bowl of soup, or their service once or twice a month shall not credible “professional” of, so to speak , an outsourcing company, which was found hanging on thanks to the bus stop ad … and it’s not a secret that the effectiveness of even perfectly adequate iT-specialists often simply no one to assess, as the company’s management, as a rule, slightly dilute raetsya in matters of IT-security, rightly believing that for this and there should be specially trained professionals. But these professionals are expensive – to hire a student, of course, easier. Well, let’s try a new series of articles devoted to information security in small and medium-sized businesses, at least in part to break this vicious circle…
But before we proceed to deal with the issues directly with the organization IT-security company, perhaps it makes sense to find out what it is – cyber threats, what they are, what dangers are, as with the help of which they can be most effectively counter. This is, firstly, give understanding – protection against any risk it is most important in a given company, and, secondly, to allow for a determination as to which funds will be needed. The fact that the protection of what is called the maximum – a thing, of course, is good, but always does it require? In some cases, enough setting the most common anti-virus for a couple of available computers, and in some cases cannot even use Windows as the operating system, or even require special measures to additional electromagnetic shielding system units and monitors to reduce the possibility of remote reading of confidential information (however, in these spheres, we have to invade will not – I repeat, it would be a most ordinary firms, enterprises and companies that are not related state secrets). Roughly speaking, on the IT-security costs – both financial and organizational – must be proportionate to the loss that you may incur in the event of the situation on the worst-case scenario.
Cyber threats today are usually subdivided into external sources and causes of which are outside of your computer and your company, usually – in a global network, and internal, depending primarily not from some abstract intruders from the Internet and from your own personnel, equipment and software.
External threats
Viruses

The external cyber threats include, in particular, all kinds of computer viruses, so-called “worms,” Trojan horses and the like malicious software secretly penetrating into the computer system. It is today the viruses are the main threat – they are encountered more than 70% of Russian companies, as to “catch” them in the absence of effective protection simple. So that they have penetrated into your computer, it may be sufficient, for example, open an attachment in an email (and not necessarily to the letter was from an unknown destination – a virus you can send and well-known partner, if the PC has appeared infected before your) or “walk” on some site with obscene (and often – and quite decent) content. Some viruses have enough of what your PC is simply connected to the same local network as your PC is already infected! The huge number of viruses used to spread “the stick”, optical media and mobile hard drives.
In short, the ways in which viruses can penetrate your network and your PC – great variety. As, however, and types of damage they can cause. But, characteristically, today’s virus writers is incomparably more often use their creations for profit rather than for fun, to amuse his misanthropy, or exercise in programming, as it was quite, seemingly recently. Suffice it to recall the scourge of the last couple of years – the virus-blockers, do not give to run Windows and require their victims to send a paid SMS-messages. However, if the Trojan virus will intercept your bank account will be even worse. Viruses destroy files adversely affect the performance of programs and computers used for their own purposes communication channels, devouring traffic, sending spam, and so on. But the most dangerous category of viruses, which appeared just recently – cyber weapons, sometimes directed at the destruction of entire industrial infrastructure. The creation of such viruses as sensational Stuxnet, Duqu, Flame, Gauss, there were probably many millions of dollars. And this is not a crafts students dropouts, behind them are very serious professionals and organizations – we know that “hackers in the civil service” is already working in the US kibervoyskah, Israel, China and Germany. The first samples of cyber weapons were directed against us from distant Iran and its nuclear centrifuges (say, not without success), but who knows what will happen next?
Spam

The second most important type of external cyber threats – for many years aroused widespread spam irritation. The percentage of spam among all e-mail today can reach 70%! Junk e-mail, urging you to buy pills for weight loss or to enroll in English language courses, spends Internet traffic, scoring links, distract from work, forcing staff to identify among advertising mountains really important correspondence that in such a situation is easy and lose (especially if you are using low-quality free spam filters with a high percentage of false positives). All of this eventually leads to financial losses. In addition, the spam – it is one of the common channels of the introduction of viruses and Trojans.
Remote hacking

Extremely dangerous remote hacking computers, whereby the intruder, who is, perhaps, at the other end of the earth, but can – in the office of competitors, is able to read and edit stored on your PC and file servers documents destroy them at will, introduce into your network of some of his programs that monitor your actions or collect some other information (down to undetectable for you video / audio surveillance through regular webcams and microphones laptops).
Phishing

Extremely dangerous so-called phishing attacks, in which the PC user “get hooked” fake web site, fully imitating, say, the bank’s website, in which he keeps his deposit. In this case, an attacker who gains all its details and passwords can easily deprive the poor man all his savings. Thrown as a “hook” is usually with the help of all of the same spam vulnerabilities in the web browser, and sometimes – and targeted attacks in which letters with links to a fake bank does not simply sent “to whom God would send” and sent to specific people, specific organizations, and with meaningful text, it is addressed to them or causing, at first glance, no particular suspicion.
DoS / DDoS-attacks
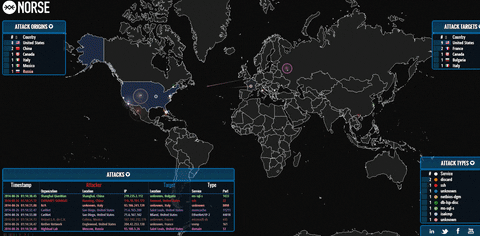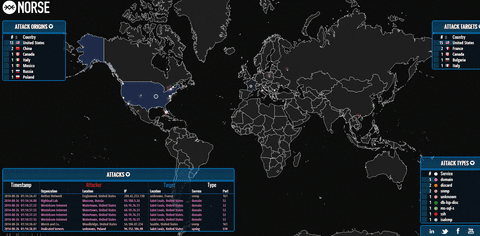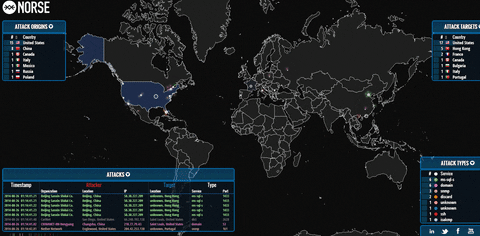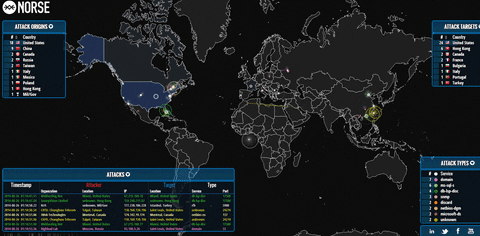
Organizations with their websites, and visible from the Internet server of other types are answered by a serious threat of DoS / DDoS-attacks, that is specially organized massive network requests fully or partially adversely affect the performance web site, email server or, say, Internet shop. Sometimes, to get rid of a rival, enough to make up its online store only a few days cannot “reach out” to potential buyers.
Theft of mobile devices
Recently, more urgent becomes the protection and on this type of external threats such as theft of mobile devices in the memory which can open a store sensitive corporate information – financial records, personal data of employees and customers, intellectual property, e-mail correspondence, various identification data and passwords.
Other external threats
This list of external threats, unfortunately, not exhaustive, and if you go beyond threats, protection of which is carried out mainly at the level of the appropriate software, you can remember, such as industrial espionage, theft of hardware of other types, or intentional infliction damage, but it may somehow another time.
Internal threats
Vulnerable
From the internal threats are the greatest threat today software vulnerabilities. Programs are written by people and for people, as it sounds banal, are fallible. Errors and omissions in popular programs, which are then detected by the most experienced hackers, and form the basis of many viruses, worms, Trojans, penetrating to the PC user through these loopholes. And the search for loopholes conducted almost purposefully, with a focus on the software installed and running almost without interruption for a vast majority of computers.
Some of these programs are installed along with the operating system (Windows is a Media Player, Internet Explorer), without the other is almost impossible to do in any of the office (for example, the familiar Microsoft Office, Adobe Reader), something has to be installed to complete the work on the Internet (java plug-in for web browsers, as well as alternative browsers such as Opera, Firefox). And, of course, is not without its vulnerabilities and the operating system – Windows, Linux, FreeBSD, iOS – no one is immune from mistakes.
As a result, the more programs used in your office, the greater the likelihood that in some of them penetrate the virus into your system. If the used software and the OS is updated regularly, from time to time, the chances of failure of the system increases catastrophically. Still, we must pay tribute to the leading software developers – the errors identified in the programs they seek to correct as quickly as possible.
However, in due time to install all the updates on the park with a computer requires some effort on the part of IT-staff. Every extra day with uncovered a “hole” in the system – unnecessary risk. Of course, the use of free (support is part of the manufacturer, as a rule, almost at zero level), and even more unlicensed software will also play in this matter only against you.
Data leakage
Soviet-era poster “Loudmouth – a godsend for a spy”, unfortunately, still has not lost its value. Accidental leakage / dissemination of sensitive data is in second place on danger. The more that modern means of communication that contribute in every possible way. ICQ, Skype, «VKontakte”, “Classmates”, simply e-mail: all of this – information leakage channels, which can be very expensive. Plus phones, tablets, laptops, “stick”, and mobile hard drives, which are regularly lost and stolen even special services, what we periodically inform news feeds.
In addition, leakage of confidential data may not be completely random, and not even intentional, with appropriate measures to conceal himself leakage fact (one of the most common ways to steal information – just a snapshot of your computer screen to open the document on your phone’s camera, if quietly bring it as it is impossible to file)
Do not forget that a leak can occur due to the fault of your partner, contractor, service provider (coming cleaners, couriers pizza, Internet provider, web hoster, and so on), and among their own employees may be caught frankly criminal element. Finally, important data can be easy to lose because of the failure of the media containing them.
Conclusion
These are the main types of cyber threats. As you can see, for the full protection of the information space of the enterprise, data storage and processing systems require not only installing the appropriate software and a set of software and technical, administrative, organizational and regulatory measures. This should be:
- protect information devices and media using hardware and software;
- established regulations governing the work of the personnel information;
- Developed a set of measures to prevent information leaks and access to unauthorized persons.
Moreover, in any one case, a special emphasis will have to do (but not in any way to the detriment of the protection of other components of the IT-systems), for example, to protect the site, the other – to protect the fleet of workstations, and in some cases have to allocate additional funds to create a failover data warehouse. In the end, everything depends on what particular type of cyber threats are most dangerous to that particular company.
